Deconstructing security identifiers: How to understand the anatomy of security identifiers
Did you know that while we often think of security identifiers (SIDs) as being numbers, they can also be strings of characters? This may seem irrelevant, but there are situations where it’s important to understand the anatomy of security identifiers and how they can be represented by both numeric and alphanumeric values. Understanding SIDs better could lead to more secure systems, networks, and applications. To learn more about this topic, check out the following article on deconstructing security identifiers.
What is a security identifier?
A security identifier (SID) is a number that can be assigned to an object in order to identify it, usually on a Windows domain. The object that gets assigned the SID becomes ‘well known’, meaning that other systems such as computers and printers will easily recognize it. SIDs are used on lots of places, including objects like computers and printers as well as users and groups, where they are often not so easy to see. It is also sometimes called just ID in these cases. The SID is made up of two parts: the Relative Identifier (RID), which identifies what type of object this is; and the domain relative identifier (DRI), which tells you who owns this object. For example, if your computer has been assigned a RID=20000 when it was first joined to the domain, then your DRI=20001.
Types of Security Identifiers
- Account Identifiers – account name, email address, IP address.
- Platform Identifiers – platform type, platform version
- Device Identifiers – device type and serial number
- Personal Identifiers – data such as fingerprint scans or other biometric information and password changes
- System Data Generators – physical security controls that generate unique system ids and associated records
When Do I Need to Know About Security Identifiers?
Not all security IDs are created equal. To be able to take advantage of two-factor authentication, for example, you will need a hardware key (like a Yubikey) that can use both a public and private keypair as proof that it is who it says it is.
When Can I Use Security Identifiers Instead of User IDs?
Security identifiers may be helpful in high-volume environments such as schools, healthcare facilities, retail stores, and government offices. A few examples of when a person’s Social Security number might be necessary are for banking purposes or filing taxes. In other instances, a person’s account number or username may serve as an appropriate form of identification.
Where Do I Find Them?
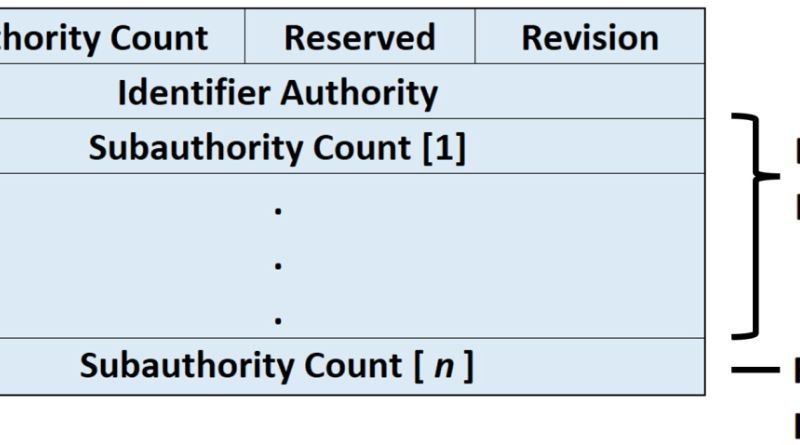
There are three components that make up a security identifier. They are: a name, value, and container. Each of these components can be broken down into many layers with different numbers (groups) or names (types). I’ll explain how each part is structured below.
First, we have the Name and Value. These two make up one individual identifier but are never shown on their own.
How Are They Used in Programming Languages?
It can be difficult for programmers without a strong knowledge of computer science to conceptualize what exactly these strings of numbers and letters mean. They may seem like nonsense. However, many programming languages use these as references or labels for data in storage, database queries, and other related areas. So what is a security identifier? It’s best to think about it in terms of how the name is written out. For example, if you were given an international social security number like 547-86-1234, you could break that down into three parts. The first two digits identify which country issued the card (in this case 547), then two more digits show which region within that country issued the card (86), and finally four more digits are your personal number (1234). If you just want to know your personal number without worrying about any of the other information then you would leave off all but those four digits.